How to check your Windows network for vulnerabilities

If you've made significant changes to your network to support remote workers, it's time to review what you've done to make sure everything is locked down.Now that you’re settling into the new normal of abnormality, it’s time to review the insecurity you might have introduced into your organization in the rush to support a remote workforce. As a recent twitter post from Jake Williams, founder of RenditionSec, noted, we’ve totally changed our networks in the last few weeks, and it’s time to scan for vulnerabilities.
Scan for exposed ports
First, scan Remote Desktop Protocol (RDP) ports that are open to the internet. Use a tool like Nessus to scan your external IP address ranges to review what is now open and needs additional security or review. If you use external scanning tools you may need approval from management as well as your internet service provider.
Ensure that any exposed remote desktop ports are set to respond only to Network Level Authentication (NLA) and preferably are either protected behind Remote Desktop Gateway (and thus only respond over port 443) or protected with two-factor authentication.
Do a second scan of your internal network to ensure that when you have RDP running, it’s enabled with NLA. If the user trying to connect doesn’t have valid login credentials, even though the RDP service is running, no RDP session will be created with NLA enabled. This prevents an attacker from enumerating low-hanging fruit such as usernames, domain names and logged-in users.
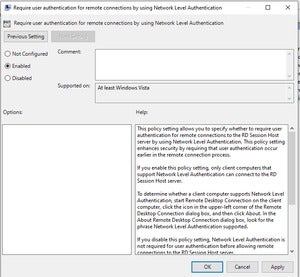
If you are running the Remote Desktop Session Host (RDSH) role on newer servers, NLA is enforced by default. If you are unsure, use Group Policy to enforce the setting. Find the setting to require user authentication for remote connections via NLA at ComputerPoliciesWindows ComponentsRemote Desktop ServicesRemote Desktop Session HostSecurity. This setting must be applied to the server running the RDSH role.
Susan Bradley
Set the Group Policy for NLA
Review firewall and DNS logs
Next, review firewall and Domain Name System (DNS) logs to look for traffic that is suddenly going outbound from your network. Make sure only authorized remote-access tools are being used. If a someone has downloaded a remote-access tool because what you’ve provided isn’t working for them, see what can be done to make their access better.
Review remote access and reevaluate the selections and solutions. Look for unauthorized deployments of TeamViewer, GotoMyPC or LogMeIn that open your firm to more access than you intended.
Use a net flow analysis tool or review your firewall traffic graphs to see what bandwidth is being used. Look for any abnormal software deployed in your organization that is taking up excess bandwidth. Review log files for any abnormal connections, particularly for outbound VPNs used as a reverse tunnel for access.
Review firewall configurations
Review your firewall configurations and pay attention to any changes in the configuration you’ve made in the last few weeks. Did you add rules for SSH? Did you change rules in the firewall to support VPN? Are these changes still needed? Could they be set up differently and more securely? Rather than opening a static port in the firewall, could it be set up with a firewall rule that reviews and scans the traffic instead? If you need guidance, ask your firewall vendor support department for assistance. Firewall rules in various platforms can be confusing or complicated to set up.
Review group changes
Review what changes were made to users in new organizational permissions groups. Are they still appropriate? (For example, look for anyone temporarily moved into an administrative group to get users working.) Can you adjust the groups to make permissions more secure? If your users are now working remotely, perhaps they no longer need full access to the same files and folders as before. Could you limit access and thus ensure that you are better protected from ransomware attacks?
Take advantage of vendors’ emergency tool sets
Finally, reach out to your security solution vendors to see if they are offering any emergency tool sets to allow you to review and scan for more issues. For example, Proofpoint is offering free COVID-19-related IDS rules to better protect their customer base.